Here’s how to make sure no one else can read your Facebook Messages
The social network that launched a thousand privacy scares is giving you a way to send messages so private that neither the company nor anybody but your correspondent can decrypt and read them.
Facebook (FB) calls this new Messenger feature “Secret Conversations,” and it not only lets you scramble messages, but it also lets you set them to self-destruct.
The catch: If you switch to this more secure mode, every message you encrypt runs the risk of self-destructing — even if you don’t want it to. But that could be a worthwhile tradeoff for knowing that your messages can’t be read by anybody but the recipient.
The social network has never offered that option before, although its Whatsapp messenger service deployed “end-to-end encryption” in April. You may not have it yet, but you soon should — the company said in its announcement that it’ll be “more widely available this summer.”
How it works
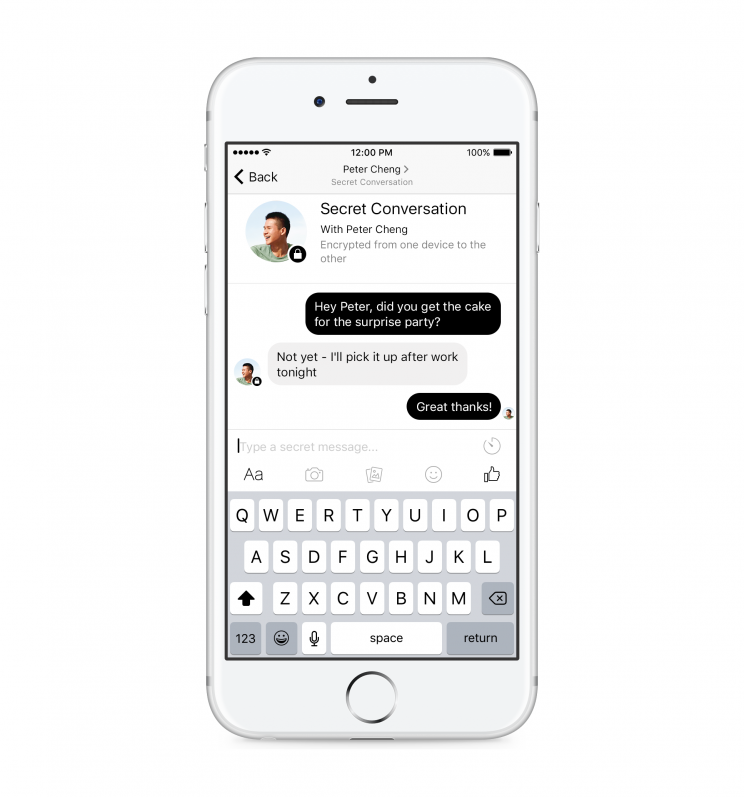
First you’ll need the latest version of Facebook Messenger for Android or iOS; they’re the only ones that support Secret Conversations right now.
Then you’ll need a strong sense of which mobile device you will keep around for a while and keep secure — you can only enable encryption on a single phone or tablet, and anybody who can unlock it can read your secret chats.
Now select a friend in Messenger, tap their name at the top of the conversation (in iOS) or the “i” in a circle at the top right corner (in Android) and choose “Secret Conversation.”

Once the recipient designates a phone or tablet as their encrypted device, you’ll open a separate thread in which your messages appear in black bubbles instead of the usual blue.
What you won’t see is a request to generate an encryption key, exchange it with correspondents or do any of the other chores associated with enabling encryption. All that happens in the background; as a Facebook white paper explains, the app generates keys on each device for each message.
Facebook only gets an “identity key” confirming that you are you; you can see yours and your friend’s in a secret conversation by tapping their name at the top of the screen and then choosing “Device Keys.”
Facebook built this function using Signal, open-source software developed by Open Whisper Systems with help from $2.3 million in funding from the government-backed Open Technology Fund. Edward Snowden has repeatedly endorsed Signal on Twitter, and the Electronic Frontier Foundation gave it a perfect score in last year’s “secure messaging scorecard.”
A Secret Conversation can include photos, emoji, thumbs-up Likes and stickers, but not voice calls, video or group conversations.
You can also set a message to self-destruct after it’s been viewed — your options range from 5 seconds to a day — by tapping the clock icon to its right. A clock will count down on both devices, after which the message vanishes … unless the recipient takes a screenshot of it.
Note that you’ll keep sending self-destructing messages to this person unless you tap the clock icon again and switch the timer to “Off.”
Issues and limitations
Facebook’s Secret Conversation is vastly easier than other encrypted options — and has the virtue of coming in an app that, as Facebook just bragged, 1 billion people use a month. Even the announced limited scale of the trial turns out to matter little when anybody with this feature can invite friends to use it.
(Security-minded Facebook friends, come at me.)
Unfortunately, Secret Conversations are chained to one device in a way that other encryption setups — including WhatsApp’s — are not. Enabling the app on a new device wipes previous encrypted messages off the old one, and even a full, encrypted backup of an iOS device to iTunes will not preserve them. So, really, every Secret Conversation is potentially self-destructing until future versions address this.

“It’s not an unavoidable limit. It’s just that adding multiple devices adds a lot of complexity,” explained Matthew Green, a cryptography professor at Johns Hopkins University whom Facebook paid to help with the project. “There needs to be a mechanism for registering many devices, for ensuring that nobody adds a device you don’t want, etc.”
For example, while I can use GPG Suite on multiple Macs to encrypt e-mail messages using the Pretty Good Privacy standard, doing so requires me to have multiple copies of the private key at the root of this cryptography system.
“Generally you don’t want to share the same key across multiple devices,” Green wrote (confession, we didn’t bother to PGP-encrypt our e-mails). “You want to have different devices with different keys, and then add or remove them from the identity that is ‘you’ so that they can receive messages from a sender.”
Adding encryption to the popular web version of Messenger would be even harder, as Motherboard’s Lorenzo Franceschi-Bicchierai explained in a post this week.
All these hangups should explain why Facebook hasn’t made encrypted messaging the default — users would rebel at finding themselves cut off from chats.
But even though “Secret Conversations” is only optional, Facebook has put secure encryption in the hands of hundreds of millions of more people. That’s something politicians should think about before they resume talking about encryption as something only criminals use.
Email Rob at [email protected]; follow him on Twitter at @robpegoraro.
